Emerging trends in phishing that MSPs should share with their SMB clients
Attackers are constantly creating new attack methods and improving upon others. What’s popular one year may not be as effective the next. In addition, hackers may tailor their attacks to specific industries, positions or even to the time of year to correspond with holidays or events.
While hackers typically evolve and alter their attacks over time, we can spot attack-types that are either new in the landscape, or make note of the types that we see increasing in frequency. The five attack-types listed below have been growing in popularity, and we’ve seen changing techniques and varying formats within these attack areas as bad actors work to improve their methods.
Share this list of emerging phishing trends with your clients:
1. Links hidden in graphics
Marketing and promotional emails are common in most users’ inboxes and often contain links to the sending company’s login or shopping page. Educated users will hover over links before clicking and may even inspect the message for inaccuracies before interacting with it. But even if all the details in a message appear accurate, bad actors may be linking the graphics inside the message to a malicious phishing site where users are prompted to enter personal details instead. By not displaying the link, the message is more likely to bypass email security tools, making it appear legitimate.

Image credit: Check Point / Tom's Guide
How users can avoid this type of attack: While your MSP can make sure your client’s users have content filtering and image blocking set up for senders that aren’t on users’ “safe senders list” in Outlook and Gmail, we can’t rely exclusively on email security tools to stop malicious links and content from landing in inboxes. In fact, in 2022 18.8% of phishing messages were able to bypass Microsoft Defender by using tactics that bypass common filters. If a user recognizes that an image is a link, they should be able to rule it out by hovering over it to check where they’re being directed. In addition, checking the link of the page they’re redirected to and attempting to access the page through the assumed-sender’s other channels is a good way to ensure your users are accessing legitimate login pages instead of a spoofed version.
2. Deep fake phishing attacks
These dangerous, AI-built attacks typically play on users’ fears by impersonating the voice and/or likeness of family, friends or business colleagues. In the attacks, bad actors may ask for money or private information to remedy a (simulated) bad situation. Urgency is also a common tactic used in these attacks as they often give users a time frame to send money within or provide another reason for urgency. While these attacks are most commonly done in real-time, some attackers may pre-record messages and send them out to a large pool of users in an attempt to extract more information or resources.
Learn more: 6 AI-related cybersecurity scams your end users should be aware of
How users can avoid this type of attack: Preparing to combat these types of attacks is best practice for avoiding them. Suggest your clients create a secret passphrase to share with their users that could be used to identify a fraudulent phone or video call. Make sure they only share this passphrase verbally and don’t send it via email or text.
3. Hybrid call-back phishing attacks
Finding new ways to bypass email filters is something bad actors have been focusing on in recent years. Hybrid attacks are a prime example of this as they’re typically plain text messages with no malicious links or content inside. Instead, the bad actor includes a phone number for the user to call and a reason for them to do so. The reason could vary, from correcting an inaccurate invoice, to updating information or even details for receiving an award. In addition, the bad actor may place a call to the user in reference to the message - connecting a phone number to a user and potentially appearing to verify the message content.
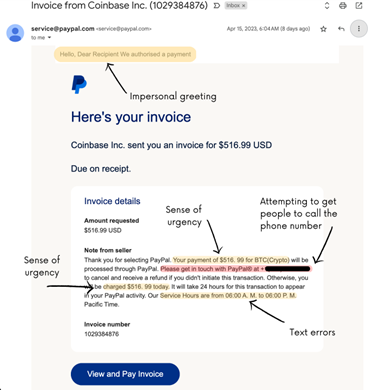
Image source: resources.hacware.com
How users can avoid this type of attack: Before placing a phone call based on an email, users should verify the call-back number by checking the real website’s customer service number or reaching out to the potentially-impersonated company through a secondary-source to verify the information. These attacks may also be avoided by ignoring calls from unknown numbers or attempting to take the required action through the assumed-sender’s actual website.
4. Business email compromise (BEC) attacks
While this attack-type isn’t new, it’s a good example of how hackers are constantly coming up with new ways to infiltrate and impersonate trusted accounts. BEC attacks increased by 81% during the second half of 2022, thanks in part to new and evolving attack methods. One subset of BEC attacks, called a reply-chain attack, starts with a hacker gaining access to a user’s email account before using those credentials to insert themselves and their malicious links or downloads into ongoing conversations.
How users can avoid this type of attack: BEC attacks are traditionally tough to detect because they appear to be coming from inside the user’s organization. The best way to avoid these attacks is by creating a culture where users are empowered to trust their gut-instincts and encouraged to double-check even slightly unusual or off-sounding requests through a secondary method.
5. Smishing attacks
While hackers have been targeting users through their phones and messages for the past few years through “missed package” scams and Covid-related attacks, smishing has been steadily growing in popularity among attackers as a way to mine user credentials. The Cloudflare and Twilio attacks showed how effective smishing can be by asking users to reset their passwords via text and stealing two-factor authentication details with spoofed login pages. These attacks are often aimed at mining personal details and building elaborate social engineering campaigns to steal information or money from unsuspecting victims.
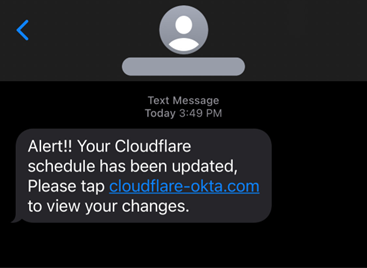
Image source: blog.cloudflare.com
How users can avoid this type of attack: The best way to train your users to recognize smishing attacks is to train them through SMS-phishing simulations. It’s also a good practice to guide users to be suspicious of every text received from an unknown or unexpected number and to only take action through a secondary medium.
As your client’s trusted MSP, providing ongoing education can be a building block toward growing their culture of cybersecurity. In addition, empowering their teams to better understand each user’s role and impact in identifying and protecting their organization against cyber attacks, as well as keeping them informed of new and emerging attacks to look out for, could lead to an increase in recognizing and reporting phishing messages when they appear in their inboxes.
Learn more about HacWare: MSP partners can decrease the likelihood their end users will click on a phishing message by 60%. Let’s work together to educate your end users with automated, AI-driven phishing simulations and under three-minute micro-trainings to keep user attention and improve learning outcomes.
Learn more about our partner program and how we can support your MSP's grow