Absolute Resilience for MSPs
We Stop Downtime. Absolute Security's firmware-embedded resilience is already built into your customers’ devices, enabling you to prevent and minimize disruption of your management and security stack and recover in minutes when cyber incidents occur. RMM, security apps, endpoints, data, and networks are always on, always connected, always protected. Complete control for you. Complete confidence for your customers.
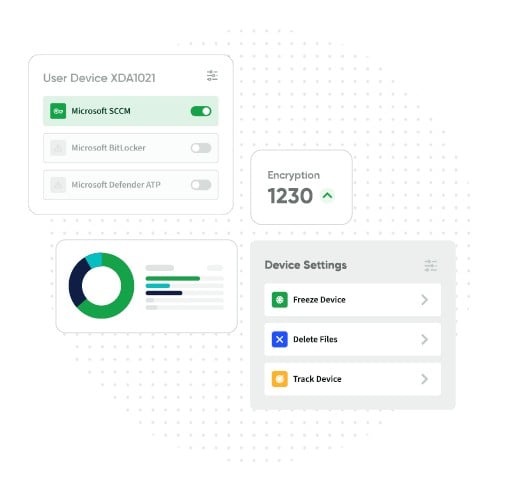
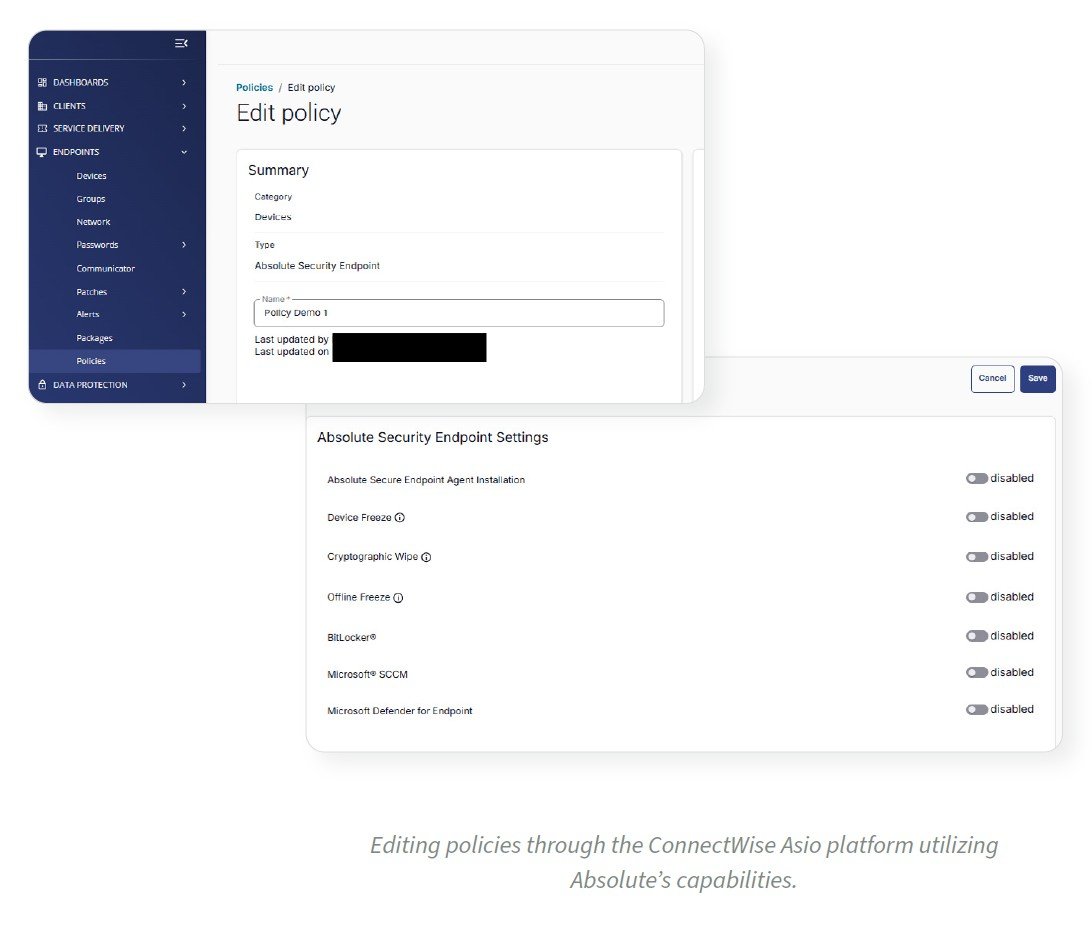
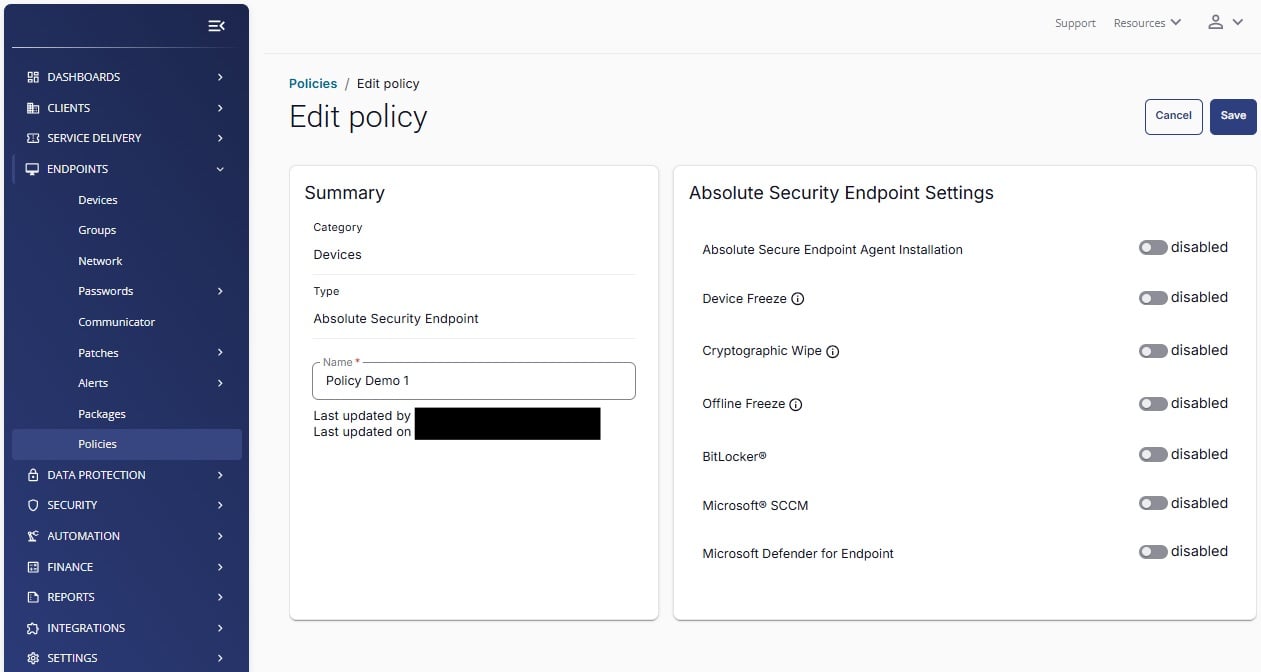
Absolute Resilience for MSPs offers Managed Service Providers (MSPs) unparalleled visibility and control across their customers’ endpoint environments. Track granular information such as device location, protect stored sensitive information, maintain the health of critical security applications and remotely respond to device risks, compliance breaches or security incidents.
Read the latest blog : From Automation to AI: How Absolute Security Turns ConnectWise’s Vision into MSP Reality

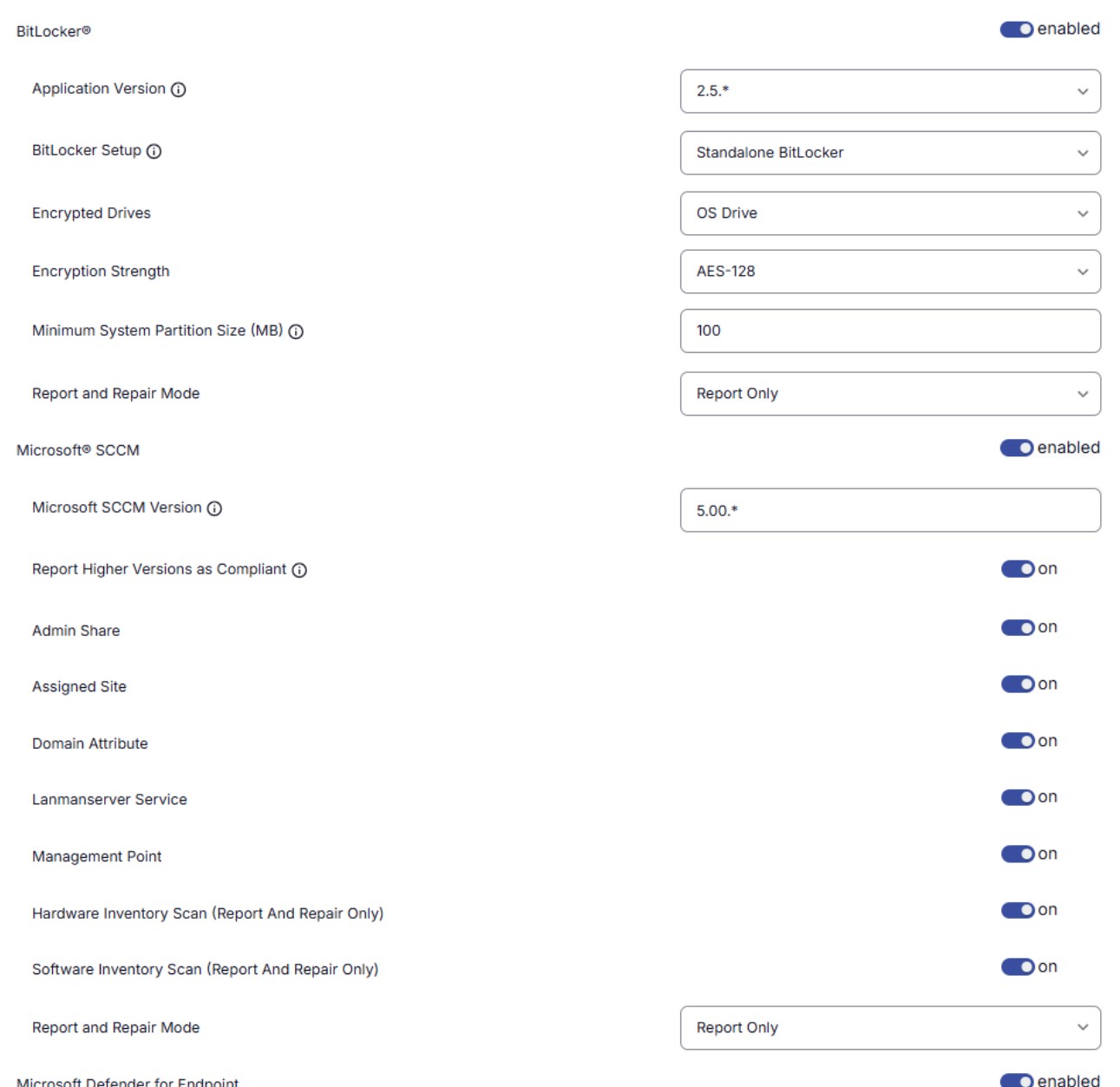
Enforce Endpoint Compliance
Monitor key device attributes and self-heal critical security apps to maintain security posture.

Rehydrate devices back to a trusted state
Restore endpoints back to a fully compliant state after an IT or security incident.

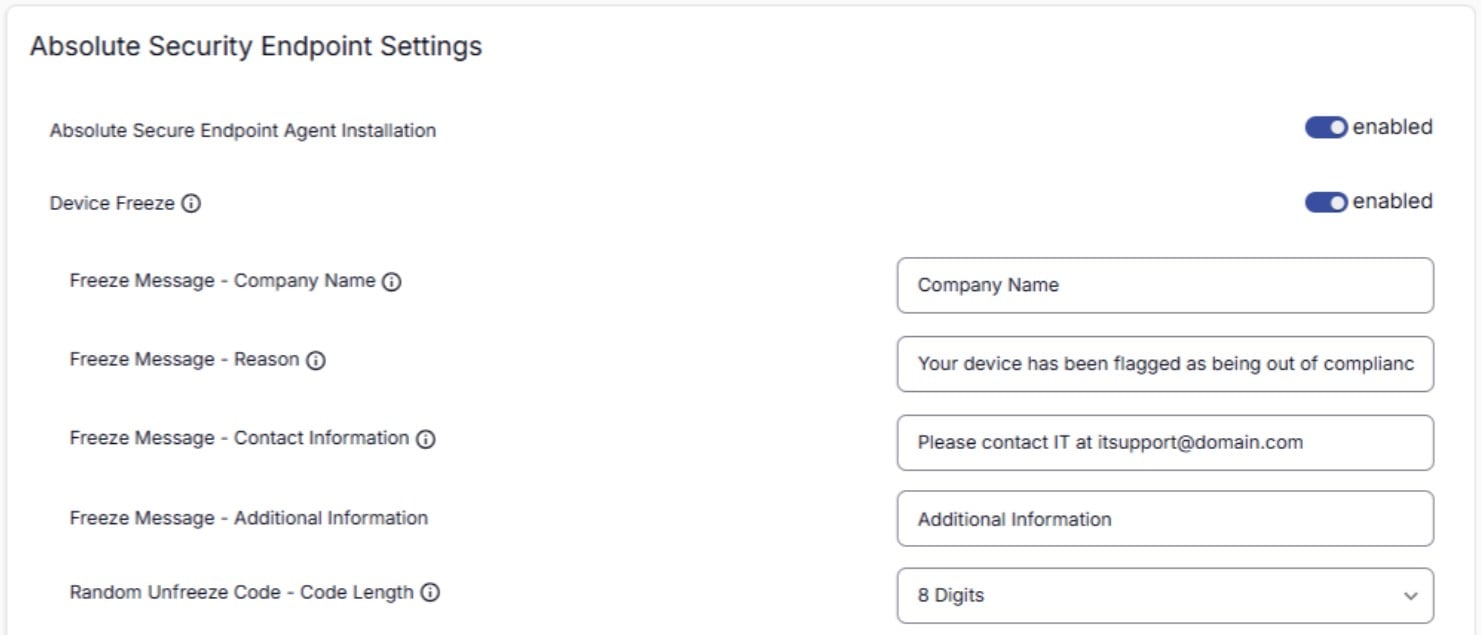
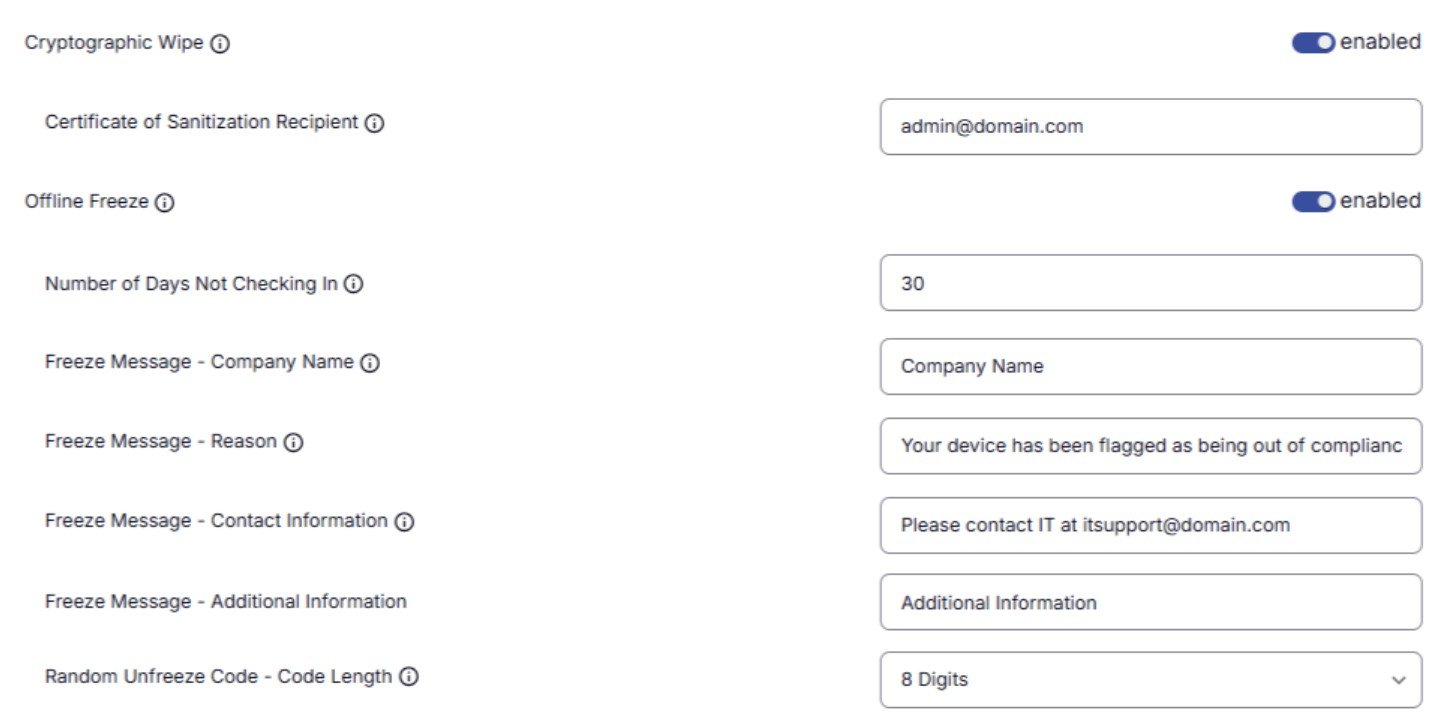
Secure At-Risk Devices and Data
Freeze compromised endpoints. Securely wipe data with proof of erasure for audits.