
Third Wall
Third Wall policies provide essential protection, locking down vulnerable protocols, limiting end user access to dangerous functions, preventing data theft and phishing, even watching for ransomware attacks.

Third Wall policies provide essential protection, locking down vulnerable protocols, limiting end user access to dangerous functions, preventing data theft and phishing, even watching for ransomware attacks.
This integration is certified via the ConnectWise Invent program, which means it was developed in collaboration with the ConnectWise API team, passed a security review, completed the certification process, and receives tier 1 integration support.
Third Wall policies provide essential protection, locking down vulnerable protocols, limiting end user access to dangerous functions, preventing data theft and phishing, even watching for ransomware attacks. Emergency action buttons let you Isolate or Annihilate compromised computers, and critical reports give your clients logon and audit information.
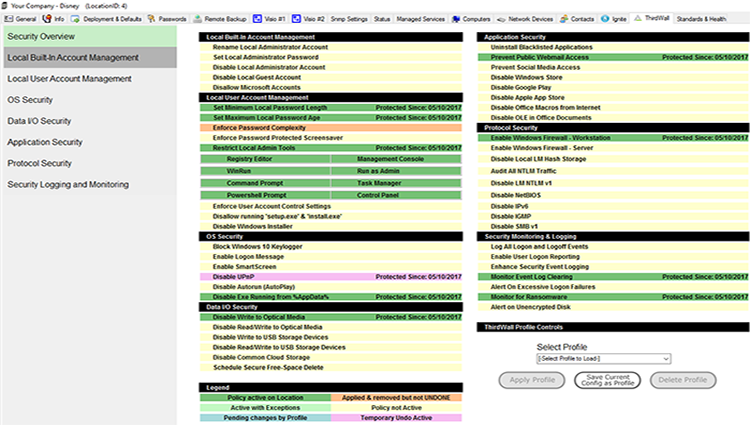
Third Wall's 56 policies can be deployed protection across a single Location, across an entire Client, or across all of your managed computers. Monitors run every 5 minutes, auto-correcting if needed and notifying you of any discrepancies. Some policies, such a Monitor for Ransomware, have hair-trigger monitors that immediately detect issues and initiate instant response to mitigate damage and prevent spread of malware. At a glance, you can see the status of every policy, and can easily change settings, apply temporary policy suspensions, even make exceptions to any computer. Third Wall makes cybersecurity protection simple for you.
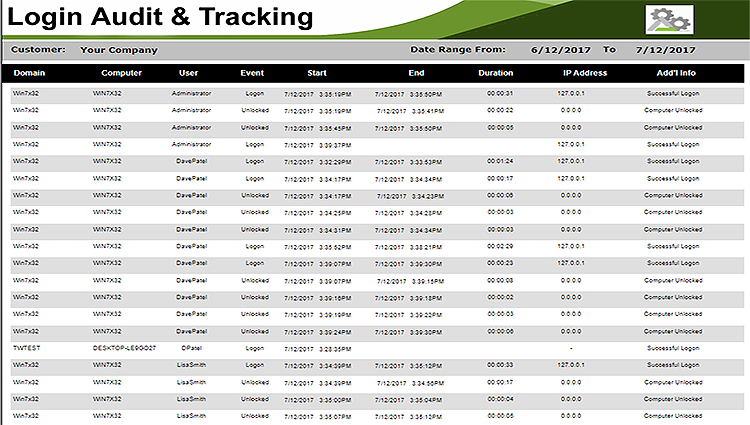
Third Wall captures critical Logon data for every client, giving you a full month look-back for every User logon, logoff, computer unlock and computer lock event. Sorted by User / Domain / Computer / Time, this report gives your clients a full record of all activity, and can show not only if someone was logged on, but also if they were working. This information is necessary for any audit compliance. The accompanying Dataview allows you to quickly answer the client question - "was someone in the office after hours last night?" Your clients want this information.
Third Wall makes you the Operational Cybersecurity expert in minutes. With powerful policies, quick-acting emergency response buttons, and indispensable reports, you and your clients need this protection. Way too much gets past firewalls and antivirus, and the primary ways in are closed off by Third Wall. Data theft by employees and contractors is rampant, but Third Wall shuts that down. Your clients are worried - as they should be - and you can be the hero who provides the best protection. Start a free, unlimited use 30-day trial at www.Third-Wall.com today, find out what it can do for you.
Requirements: Third Wall Version 2.0.5.4 and above are certified to work with all Automate 12 and 2019 versions. As a standalone plugin, it does not integrate other products into Automate.
Features:
If you need assistance with creating API members or integration setup please send a note to Help@ConnectWise.com and the ConnectWise PSA support team can assist. For any other questions with this integration, please contact the vendor directly to resolve any issues.
Coming soon.
Coming soon.
Third Wall policies provide essential protection, locking down vulnerable protocols, limiting end user access to dangerous functions, preventing data theft and phishing, even watching for ransomware attacks. Emergency action buttons let you Isolate or Annihilate compromised computers, and critical reports give your clients logon and audit information.
Third Wall's 56 policies can be deployed protection across a single Location, across an entire Client, or across all of your managed computers. Monitors run every 5 minutes, auto-correcting if needed and notifying you of any discrepancies. Some policies, such a Monitor for Ransomware, have hair-trigger monitors that immediately detect issues and initiate instant response to mitigate damage and prevent spread of malware. At a glance, you can see the status of every policy, and can easily change settings, apply temporary policy suspensions, even make exceptions to any computer. Third Wall makes cybersecurity protection simple for you.

Third Wall captures critical Logon data for every client, giving you a full month look-back for every User logon, logoff, computer unlock and computer lock event. Sorted by User / Domain / Computer / Time, this report gives your clients a full record of all activity, and can show not only if someone was logged on, but also if they were working. This information is necessary for any audit compliance. The accompanying Dataview allows you to quickly answer the client question - "was someone in the office after hours last night?" Your clients want this information.

Third Wall makes you the Operational Cybersecurity expert in minutes. With powerful policies, quick-acting emergency response buttons, and indispensable reports, you and your clients need this protection. Way too much gets past firewalls and antivirus, and the primary ways in are closed off by Third Wall. Data theft by employees and contractors is rampant, but Third Wall shuts that down. Your clients are worried - as they should be - and you can be the hero who provides the best protection. Start a free, unlimited use 30-day trial at www.Third-Wall.com today, find out what it can do for you.
Requirements: Third Wall Version 2.0.5.4 and above are certified to work with all Automate 12 and 2019 versions. As a standalone plugin, it does not integrate other products into Automate.
Features:
If you need assistance with creating API members or integration setup please send a note to Help@ConnectWise.com and the ConnectWise PSA support team can assist. For any other questions with this integration, please contact the vendor directly to resolve any issues.